Secrets Management and Sensitive Data Protection
Encryption
It is allowed to store values of the properties in the encrypted form.
VIVIDUS uses Jasypt (Java Simplified Encryption) which provides two-way
encryption mechanism. While performing two-way encryption, apart from feeding
plain-text it’s required to feed the secret text (i.e. password) and this secret
text is used to decrypt the encrypted text. The default encryption algorithm is
PBEWithMD5AndDES.
How to encrypt a string
Option 1 (Recommended): using Jasypt CLI
-
Download the latest Jasypt release
-
Unpack the downloaded zip-archive
-
Go to
binfolder -
Run the command performing encryption:
Example 1. Windows:encrypt.bat input="This is my message to be encrypted" password=MYPAS_WORDExample 2. Linux/UNIX/macOS:./encrypt.sh input="This is my message to be encrypted" password=MYPAS_WORDwhere
-
input- Any string to be encrypted. -
password- Your encryption password.MYPAS_WORDis a sample password and should be never used, own strong password is required for the encryption.
-
-
Find the encrypted data in
OUTPUTsectionExample 3. Encryption command output----ENVIRONMENT----------------- Runtime: Eclipse Adoptium OpenJDK 64-Bit Server VM 17+35 ----ARGUMENTS------------------- input: This is my message to be encrypted password: MYPAS_WORD ----OUTPUT---------------------- WVnXhzG704KRZZFYL7hfpA4YoSm8V2F5eNXyr7CRYCichteHvNS3nB23zaI8CuLy
| Find more details in Jasypt CLI Tools documentation |
Option 2: using Jasypt Online
| Use this tool at your own risk, since there is a chance of potential leakage of sensitive data |
-
Paste plain text string to encrypt to the corresponding text field.
-
Set Type of Encryption to "Two Way Encryption (With Secret Text)".
-
Enter secret key/text in the corresponding text field.
-
Click "Encrypt".
-
The resulting encrypted string can be copied from the corresponding field.
How to use an encrypted string
-
Set the password in one of the following ways:
-
Pass the key with its password-value into a test run using command line:
./gradlew runStories -Pvividus.encryptor.password=MYPAS_WORD -
Add the password to the system project properties as the value of:
system.vividus.encryptor.password=MYPAS_WORD -
Set via OS environment variable
VIVIDUS_ENCRYPTOR_PASSWORDKeep in mind that a password specified in the command line takes priority over the project system property, and the project system property takes priority over the environment variable.
This password must be kept secret and must not be committed to version control system. MYPAS_WORDis a sample password and should be never used, own strong password is required for the encryption.
-
-
Use the case-sensitive wrapping
ENC(…)for any encrypted property value. e.g.http.auth.password=ENC(WVnXhzG704KRZZFYL7hfpA4YoSm8V2F5eNXyr7CRYCichteHvNS3nB23zaI8CuLy)
Please see Externalized Configuration section to get more information on how encryptor password can be passed to the tests.
Secrets Management Tools
HashiCorp’s Vault
Configuration
Firstly, it is required to configure Vault endpoint and authentication method.
| The properties marked with bold are mandatory. |
| Property | Description | Example | ||
|---|---|---|---|---|
|
Vault enpoint |
|||
|
Token authentication requires a static token to be provided.
|
|
||
|
Vault Enterprise allows using namespaces to isolate multiple Vaults on a single Vault server. This feature is not supported by Vault Community edition and has no effect on Vault operations. |
|
How to refer Vault secrets
-
Find the required secrets in Vault.
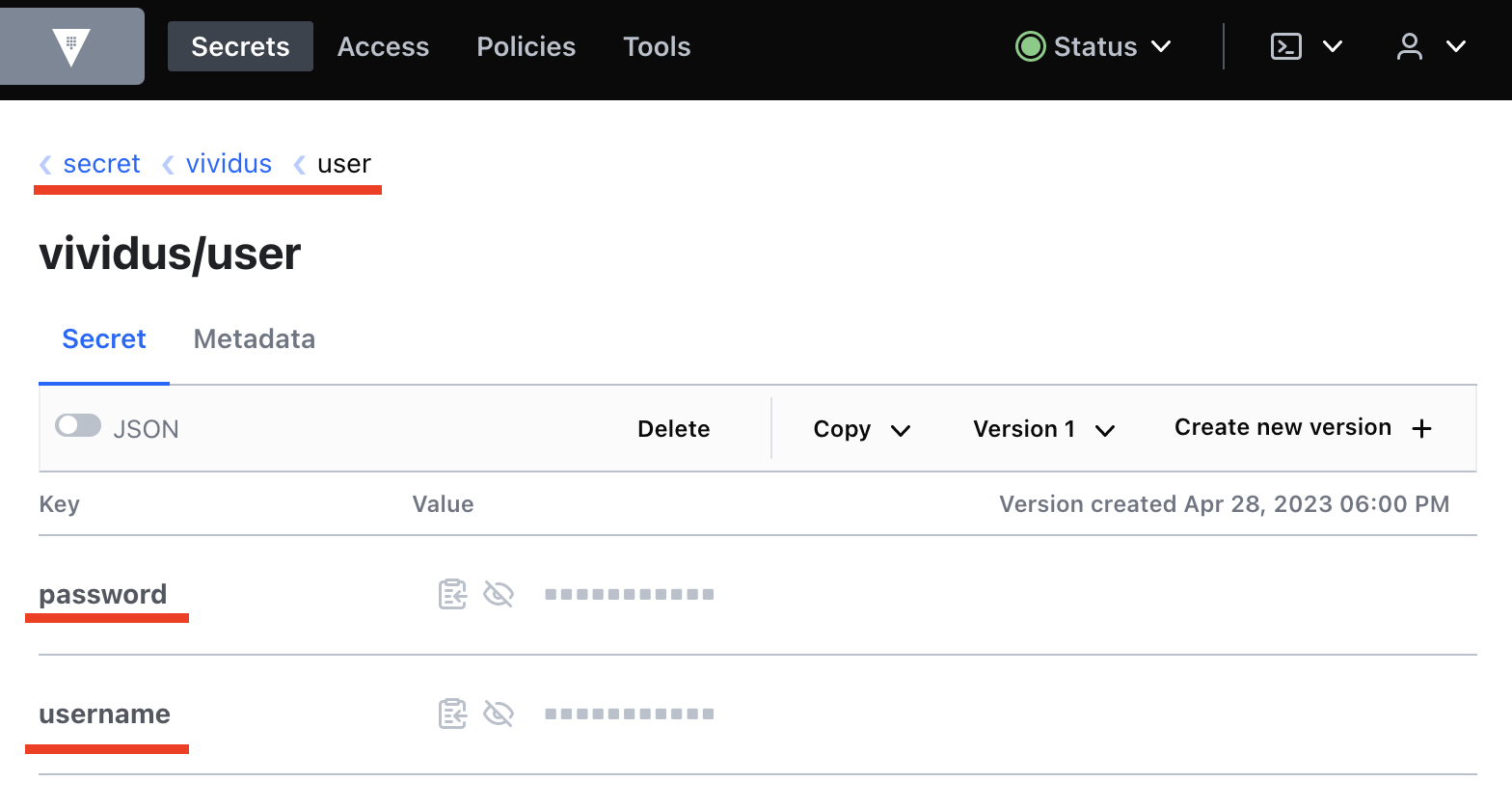
-
Build full paths to the secrets. For the secrets listed above, the paths would be
secret/vividus/test/usernameandsecret/vividus/test/password. -
Put the built paths to properties using the case-sensitive wrapping
VAULT(…)db.connection.test.username=VAULT(secret/vividus/test/username) db.connection.test.password=VAULT(secret/vividus/test/password)